Interesting Citrix/Windows information disclosure vulnerability
It seems to be just a small vulnerability and maybe fixable by simple configuration, but I found it neat. I was playing around with a application session on a Citrix environment thas has been properly "locked down" in a way that I could not see the contents of the local drives. Well, I should not be able to see that, but in fact, I found an interesting (and probably possible to be automatically exploited by client side scripts) way to bypass those controls. I started by opening a common file browse dialog (such as those you get when you choose "Save As") and using it to create a new shortcut (right button, "new", "shortcut") somewhere where I could write to. By doing it I've got the "Create Shortcut Wizard":

It seems that Windows provide some sort of "auto-complete" feature in that text box where I should input the full path for the shortcut. So, by typing just "C:" without pressing Enter I've got a drop down list with everything, folders and files, under "C:". I could potentially see everything on that volume (the NTFS permissions still work - specifically the "X" bit - I can't list the contents of the Administrator profile folder) just by typing the path and waiting for Windows to show me the options in that drop box. You can see how it looks like in the pictures below:
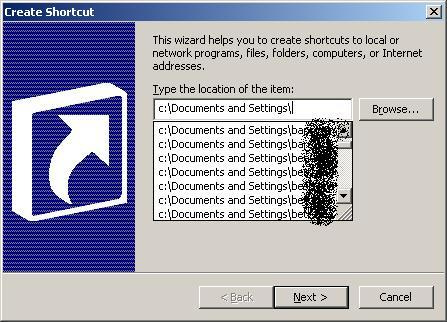
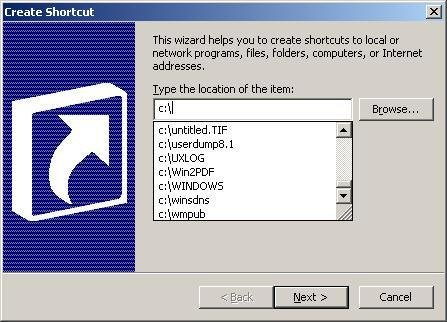
As the browsing restriction is, AFAIK, related to the explorer.exe process only, it ends up that I could also go ahead and create shortcuts to those files and use them to access the files through the published Citrix applications. Small issue, but knowing that administrators tend to leave important scripts, dump files and other stuff on servers and those often "hidden" files in published web folders, it could end up being used by a regular Citrix user to access privileged information.
Is anyone aware of any settings that could be used to disable this "path name suggestion" feature on Windows?
UPDATE: The Group Policy item used to hide drives is called Hide these specified drives in My Computer, and it's described here. However, I couldn't find anything so far that prevents the behaviour I described above.

