Simple but dreadful, part 1 - Logon Scripts
Now that I'm back to pen testing I'm having the chance to see the mistakes that admins are going into nowadays. There is something very interesting that Windows domain administrators sometimes forget and needs to be addressed as it brings serious security implications: login script files permissions.Login scripts are those little batch scripts that run when the user is logging in. They're usually stored in a share at the domain controllers called NETLOGON. The risk here is quite obvious; if I can modify your login script, I can run commands under your user account when you are logging on. This is usually not possible as the NETLOGON permissions are usually set accordingly, being writable only by domain admins.The problem is that login scripts are one of those complexity beasts that grow together with the organization and its network. Big organizations usually have lots of servers, file servers, domains and other stuff. The admins struggle to keep user lives a little easier by automatically mapping network drives, cleaning temporary file transfer areas and other stuff, and the login scripts are a good tool to do that. When doing that they sometimes need include some different command line utilities, as the regular Windows shell doesn't have all the features needed by those very creative admins. When doing that, they usually place those executables on network folders accessible by all users (of course, as they need those files during the login process :-)). What happens is that when doing that they often give too many rights for the users on those folders. Remember, when you create a folder and then share it on a Windows Server without changing any permissions there is a big chance that it will be a "Everybody - Full Control".
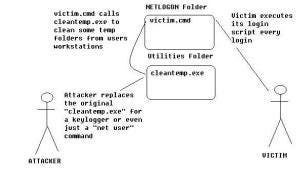
If you are a domain admin in a organization that extensively uses login scripts, check them for external executable references. Tampering with login scripts is a easy way for a insider to steal credentials and information from other users without being detected.

